Introduction
The use of wireless communication has rapidly evolved mainly with the increase in smart devices, tablets, IoT devices, and so on. Wireless connectivity has huge benefits in matters of mobility and flexibility, but its security inherently differs from security in wired networks. Information transmitted through airborne means can simply be tapped by anyone especially if proper security measures have not been adopted. Therefore, the protection of wireless communication from cyber criminals is a prime concern.
In this article, we will discuss the effects and usage of HT12D decoder IC in improving the security of wireless communication applications. The HT12D is widely applied as an encoder/decoder IC in wireless systems where addressing and identification are used. Furthermore, it is shown that by adding additional layers to the decoding and/or encoding schemes of wireless protocols, eavesdropping or hacking the signal becomes more challenging.

We will start with an overview of security threats faced in wireless networks. Then we will provide a brief introduction to the HT12D IC and understand its working mechanism. After that, we will discuss various techniques using which the HT12D can augment wireless communication security like address scrambling, encrypted data transmission, remote authentication, etc. Examples of each of these are going to be provided based on the actual case scenarios. Finally, we will briefly review the findings on the cost-effective use of HT12D for enhancing the wireless network against cyber attack solutions.
Security Threats in Wireless Networks
Let us first understand the main security threats that wireless networks are vulnerable to:
Interception – Since signals are transmitted throughout the air intercepting radio signals transmitted within the close vicinity of the attacker is fairly easier without being detected by the sender or the receiver as long as the attacker is within proximity to the transmitted signal even with the use of a software-defined radio.. This enables them to expunge undesired information such as login details, bank details, etc., which are being transmitted through the air.
Man-in-the-middle attacks - A malicious third party can insert itself between two wireless devices that are communicating and pretend to be each of the devices to the other. This way, all traffic can be intercepted and manipulated.
Denial-of-service attacks - An adversary can overload the network by constantly sending a high volume of traffic to disrupt normal functioning or drain the batteries of devices. Wireless jamming also falls under this category.
Hijacking/Spoofing of devices - A hacker can cause one device to disconnect from the network and assume its identity by using a similar one. Subsequently, all communications meant for the original device can be intercepted or misused.
Lack of access control - Wireless networks are often open and do not require any authentication. An adversary can simply connect to the network and access resources without permission.
Insecure firmware updates - Most IoT and wireless devices support over-the-air firmware updates. But if the update process is not properly authenticated and encrypted, a man-in-the-middle can replace legitimate firmware with a malicious version to compromise devices.
The above threats arise because wireless communication happens in an open broadcast medium without physical barriers. Strong cryptographic protection, access control, and authentication mechanisms are required to make wireless transmissions resistant to cyber-attacks. This is where the HT12D IC-based solutions come into play.
Strengthening Security for Industrial Wireless Networks
Wireless connectivity in the industrial landscape has offered new possibilities for performance improvements but has exposed the systems to cyber threats. Industrial control systems that oversee such critical infrastructures require a very effective defense mechanism against threats that can interfere with operations or corrupt process integrity.
HT12D solutions are well-suited to enhance security for industrial wireless networks (IWNs). The IC's address scrambling and encryption capabilities prevent unauthorized access to real-time production data flowing between machines and controllers. Control commands are only executable by authenticated devices, minimizing the scope for sabotage.
Periodic device authentication using challenge-response protocols establishes the legitimacy of nodes on the network. Should a field device's firmware or software configuration deviate from expectations, the issue can be detected through remote attestation without interrupting manufacturing workflows.
Any behavior anomalies across the IWN that could indicate intrusion efforts are detectable using on-device monitoring powered by the HT12D's processing ability. Autonomous remediation limits the window for sabotage even without human oversight.
Together these features strengthen access governance, data confidentiality, system integrity assurance, and anomaly response for industrial operations supported by wireless automation. Organizations gain robust protection of physical processes from emerging cyber threats emanating from both internal and external surfaces. Continuity of mission-critical functions receives a boost through resilient OT security powered by distributed HT12D solutions.
Introduction to HT12D Encoder/Decoder IC
The HT12D is one of the well-known Encoder/Decoder ICs introduced by Holtek Semiconductor Inc., and the IC is widely applied in wireless addressing and authentication.

Some key features of the HT12D include:
- Address recognition: It can recognize a 12-bit address in the preamble of an incoming signal and identify if it matches the internal address code stored.
- Encoding: The address can be encoded and modulated onto the carrier wave before transmission to provide secure identification.
- Decoding: At the receiver end, it can decode and match the address code embedded in the signal against the internal code for validation.
- Low power: The IC operates at a low voltage of 2.5-5.5V and has an ultra-low power consumption of only 2uA which makes it suitable for battery-powered wireless devices.
- Small package: It comes in a mini SOP-8 package with a small footprint allowing easy integration into compact wireless modules.
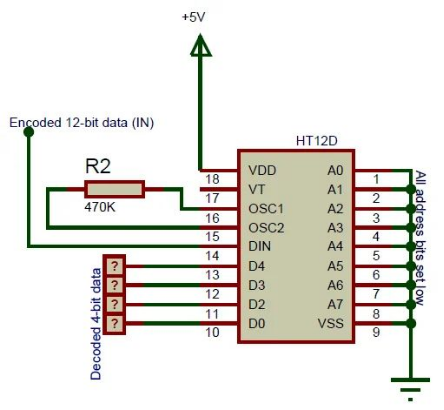
In essence, the HT12D acts as an electronic identification tag embedded in wireless devices. When powered up, it can listen for signals bearing its stored address and react only to authorized transmissions meant for it. Likewise, it can modulate a device's identifying address onto signals it transmits for verification by receivers.
This addressing and recognition capability of HT12D opens up possibilities to incorporate various security-enhancing techniques into wireless protocols as we will see next.
Address Scrambling for Cryptographic Protection
A basic way the HT12D enhances security is by scrambling device addresses cryptographically transmitted over the air. Normally addresses are sent in plain numeric format like 000100110111. But an eavesdropper can easily steal identities by listening.
With HT12D, the transmitted address can be scrambled by XOR-ing it with a pseudo-random bit stream generated using a secret key also stored in the IC. Only receivers with the matching key configured can unscramble the address.
For example, if the plain address is 000100110111 and the encryption key is 010101010101, the scrambled address would be:
000100110111
XOR 010101010101 = 010001100110
Now even if intercepted, the scrambled bits do not reveal the actual device ID without the decryption key. Only intended receivers possessing the right key can decrypt. This effectively prevents address spoofing while maintaining low transmission overhead.
The scrambling key can also be periodically changed to further strengthen security. Through such simple encryption, HT12D introduces a cryptographic layer without a significant increase in cost or complexity for resource-constrained wireless modules. Devices no longer need to fear visible identification over insecure air interfaces.
Remote Authentication using Challenge-Response
Apart from scrambling, HT12D facilitates the implementation of advanced remote authentication mechanisms between wireless devices as well. A widely applied technique is challenge-response authentication leveraging the IC's addressing capabilities.
Here, one device acts as an authentication server and can challenge any other device attempting to join or access the network by sending a random number. The challenged device encrypts this number internally using the secret key stored in its HT12D and sends back the response.
Only if the response matches after decrypting at the server end using the same key, is the connection approved.
An example flow:
- Server challenges with random# 1234
- Client HT12D encrypts 1234 using key
- A client sends back an encrypted response
- The server decrypts the response using the same key
- If matches 1234, authentication successful
By checking the device can encrypt-decrypt challenges correctly, its genuine identity gets remotely verified without physically touching it. Attackers not possessing the internal key cannot forge valid responses. Periodic re-authentication also prevents compromised devices from staying on the network indefinitely.
Remote attestation is another way the challenge-response paradigm using HT12D enhances system integrity by allowing remote validation of a device's firmware and software state. This forestalls intrusions even after physical access is gained.
Securing Wireless Connectivity in Smart Homes
The above-discussed HT12D-based techniques find prevalent usage in securing emerging wireless applications across many domains like connected homes, factories, healthcare, and more. Let's examine one such scenario in more detail.
Smart homes today comprise a myriad of interconnected wireless devices like security cameras, IoT locks, sensors, appliances, and assistants integrated under a common network. While convenient, the ALWAYS OPEN nature poses risks if not properly safeguarded.
Using address scrambling, device authentication, and secure OTA firmware updates powered by multiple HT12D ICs embedded in each component significantly elevates a smart home’s overall security posture.
For instance, camera feeds could employ periodically changing encryption keys to foil hackers from viewing live video feeds even if networks are temporarily compromised. Door locks may authenticate users through challenge-response before unlocking wirelessly.
Sensors could encrypt sensor readings end-to-end to maintain privacy. Critical systems get remotely validated for unauthorized software tampering. Problems spotted can swiftly be rectified over the air via encrypted firmware updates.
Overall a smart home built on distributed HT12D-based security architectures ensures safety, privacy, and resilience against the growing sophistication of cyber threats without the demand for heavy computing at edge nodes. Homeowners achieve assurance from a click of an app that their smart systems are reliably shielded while leveraging the benefits of connected convenience.
Strengthening Industrial Wireless Applications
Critical industrial infrastructures like factories, utilities, and transportation are also progressively digitizing processes and machines through industrial wireless networks (IWNs) to improve productivity, quality, and efficiency. However, these networked control systems managing physical processes become attractive targets for cyber espionage and sabotage if left unprotected.
Deployment of HT12D IC-based mechanisms brings essential safeguards to IWNs against various cyber risks. For instance, real-time production data communication between machines, controllers, and overseers requires the strictest access control plus data confidentiality and integrity.
Address scrambling paired with user authentication based on challenge-response prevents any rogue device from plugging into operational technology networks and manipulating industrial control commands maliciously under fake identities.
Periodic inventory checks and remote attestation of field devices ensure conformity to expected configuration baselines without disruption of process workflows. Only legitimate software upgrades can pass scrutiny and be installed over the air.
In addition, any unauthorized intrusion attempts into controllers are detected proactively through behavioral anomaly detection running on-device, and corrective actions get triggered autonomously without human oversight immediately reducing the scope for sabotage.
With wireless industrial protocols strengthened through distributed embedded security hubs, organizations gain peace of mind that critical national infrastructure and manufacturing are shielded from disruption or data theft even if hackers breach traditional IT perimeters. Overall continuity of operations is strengthened significantly.
Securing Connected Healthcare Through HT12D
Connected medical systems leveraging wireless technologies also constitute another vital domain where HT12D solutions play a key role in bolstering the protection of sensitive patient information as well as regulated medical devices.
Bluetooth-enabled health trackers, monitoring equipment, infusion pumps everything communicating vital diagnostic readings need bulletproof access governance lest any improper access puts lives at risk.
Through authenticated shared key encryption of medical records flying between doctors, pharmacies, and insurers; spontaneous hacking or leakage of Personal Health Information is effectively avoided. Similarly, wireless medical equipment identities remain anonymous from eavesdroppers through dynamic address scrambling.
Remote attestation permits validating conformity of medical device control firmware to regulatory guidelines avoiding hazardous software bugs due to unauthorized modifications. Tamper-proof OTA updates make sure approved changes aren't altered maliciously en route installation.
Authentic patients get seamless access to their health data exclusively on validated client apps shielding data misuse. Caregivers maintain control of who can switch on/off assistive patient monitoring appliances even from a distance.
Overall a medically certified, functionally segregated, and cryptographically locked down connected healthcare system prevents nefarious agents from potentially weaponizing people's medical profiles or compromising critical care equipment. Patients gain assurances of safety and HPIPA compliance with their wireless care services.
Benefits of Adopting an HT12D-Based Security Approach
To summarize some key advantages of augmenting wireless security architectures with HT12D-based techniques:
- Cryptographic protection: Encoding/decoding capabilities enable the implementation of strong encryption schemes for authentication and data confidentiality without heavy computing overhead even on resource-constrained devices.
- Tamper resistance: Sensitive data and credentials remain secure even if physical devices get compromised since secret keys never leave the protected microcontroller environment of the IC.
- Plug and play: Out-of-the-box support is provided for common wireless protocols without extensive customization required by vendors. Easy to rapidly deploy network security.
- Scalability: Distributed methodologies suit high device deployments across geographical expanse due to self-contained decentralized security functions on each node.
- Cost-effectiveness: At under $1 per unit, the HT12D presents a highly affordable means of bolstering wireless security posture as compared to alternative approaches.
- Compatibility: Works seamlessly with established LPWAN, Bluetooth, Zigbee, and other wireless standards without disruption of existing frameworks.
- Reliability: Robust encryption and authentication mechanisms upheld by ASIC logic realize ultimate dependability under any real-world environmental conditions over long operational lifespans.
In summary, through its flexible yet robust security-centric design, the HT12D IC empowers cost-efficient protection of wireless networks from a myriad of growing cyber risks in industries as diverse as industrial control, smart homes, healthcare, retail, and so on. Distributed encryption and authentication backed by the cryptographic root of trust establishes an effective shield against both passive and active threats on the air interface and beyond.
Conclusion
In this article, we explored how the HT12D encoder/decoder IC presents a pragmatic approach to significantly reinforce security for wireless communication systems across diverse application domains.
Leveraging the IC's inbuilt capabilities for network addressing, encoding, decoding, and symmetric key encryption - robust mechanisms around cryptographic protection, access control, device authentication, and secure firmware updates become implementable without major overheads.
Concepts illustrated like address scrambling, challenge-response authentication, and remote attestation demonstrated techniques through which HT12D strengthens resilience against common wireless threats. Real-life examples in the domains of smart homes, healthcare, and industrial control showcased the practical utility.
Stated benefits of embedding security in such a distributed manner using the ultra-cheap yet extremely capable HT12D chip was discussed in terms of confidentiality, hardware tamper protection, system scalability, and system dependability. As attack surfaces of wireless connectivity have grown, HT12D presentation is a perfect way for organizations to enhance their network security postures affordably.
Inherent capabilities for wireless identification within compact packages deliver assured protection of sensitive communications and endpoints from passive interception to active intrusions, establishing a strong shield for businesses as well as safety critical deployments to securely embrace the benefits of wireless digital transformation with confidence.

Comment